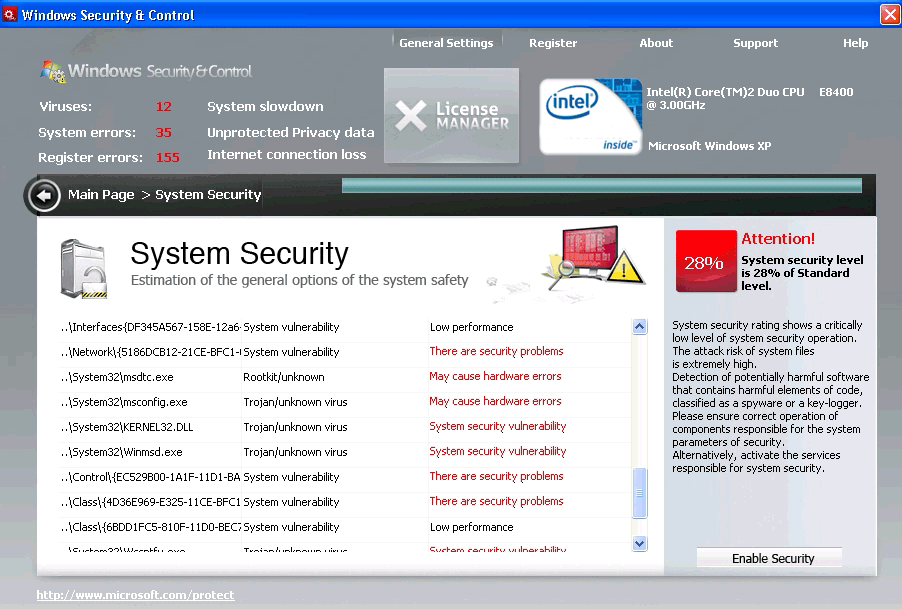
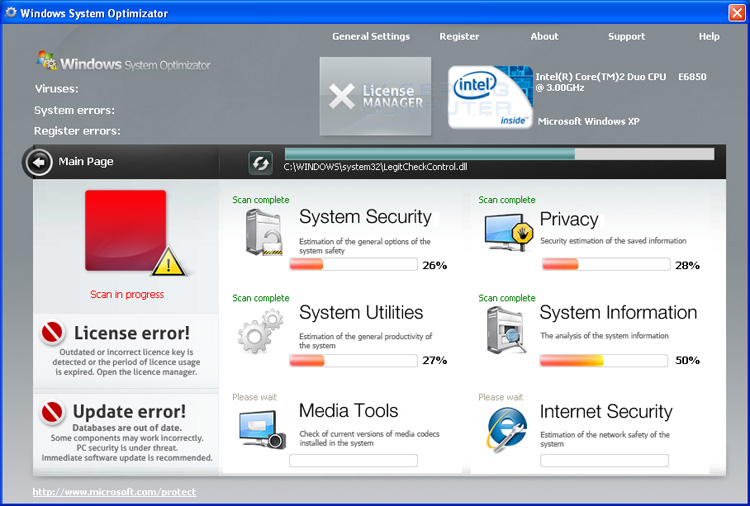
Windows Security & Control is yet another rogue security application , it is also a clone from the following rogues : Windows System Optimizator , Windows Optimization Center and Windows Optimization & Security
As we look at those clones , they are much intended to infect like other clones it blocks applications , invade safemode disable system restore and disable legitimate microsoft security essentials including real time protection
The program nothing founds only an imaginary system error and viruses by also implant itself at startup to stop the errors is to purchase key or patch the program to stop errors.
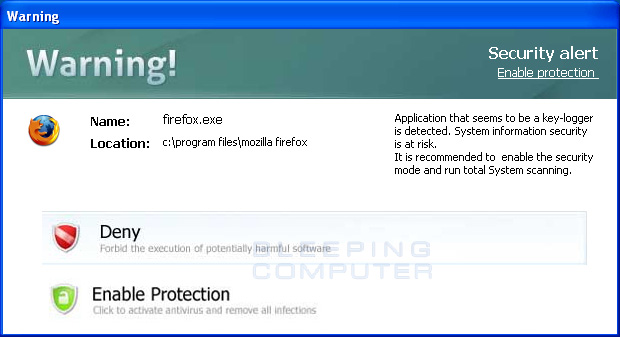
The virus use the fake microsoft security essentials alert and install but at next restart the virus replace the shell with himself.
Even if you dont know the virus hide itself in %appdata% with a random of characters it can be :
tvvdeo.exe
dxkovi.exe
frdkiu.exe
xhbvkt.exe
dnvavl.exe
jhtmch.exe
ixrojp.exe
lsjqxr.exe
udsydv.exe
lcvecw.exe
bcgtmj.exe
dvedrq.exe
yhgkbq.exe
lfkrwf.exe
ghqnrt.exe
Even if you dont heart they are the same application but randomized letters
The virus is called SecurityScanner.exe and had an md5 hash : 7dde6427dcf06d0c861693b96ad053a0
Once registered it stop blocking applications and let use legitimate antivirus to remove it
Thanks to Ender's show (File captured on 2017)